Prerequisite Configurations for AWS Secret Manager
Before implementing AWS Secret Manager, make the following configurations:
- An IAM policy, with permissions to retrieve secrets from Secret Manager.
- Your secret stored in Secrets Manager, for example
platsecret,campsecret, andplansecretwith keysPLATFORM_DATABASE_PASSWORD,CAMPAIGN_DATABASE_PASSWORD, andPLAN_DATABASE_PASSWORD:- keys should match the configMap entries
- encryption key value must be aws/secretsmanager
- A
useroriamserviceaccountthat can modify your Kubernetes cluster. - To the Docker registry, push the new set of images.
- To use the new image tags, update the values.yaml file.
- In the Helm chart, comment out the following
_PASSWORDparameters from the configMap.yaml files:CAMPAIGN_DATABASE_PASSWORDPLAN_DATABASE_PASSWORDPLATFORM_DATABASE_PASSWORD
- In the common-configMap.yaml file, add the following
parameter:
TOMCAT_FACTORY: "com.unica.manager.tomcat.utils.TomcatDSFactory" - Create secrets for the following Unica products with the corresponding
names:
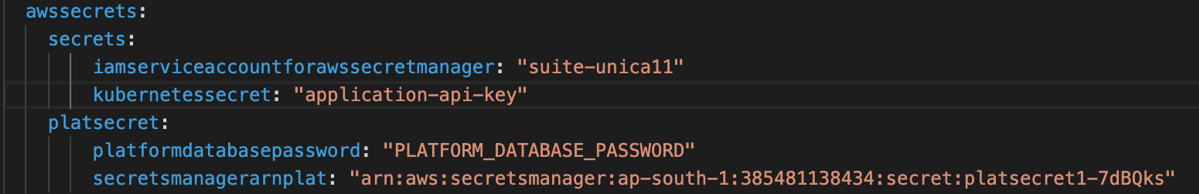
Unica Porduct Secret name Unica Campaign campsecretUnica Plan plansecretUnica Platform platsecret - Update the secret arn, secret name, and key in the following files (see the
example for reference):
- values.yaml
- deployment.yaml
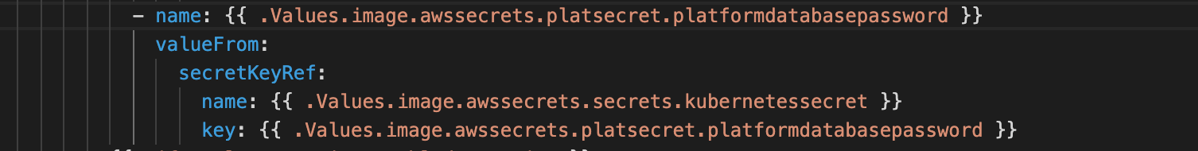
- values.yaml