Generate encrypted data (wcs_encrypt)
The wcs_encrypt utility encrypts sensitive information with a merchant key. The value of the merchant key is specified through command-line arguments or retrieved from calling out to the Key Locator Framework by using the -k parameter. If the merchant key is not specified and the parameter -k is not used, the utility encrypts the sensitive data with an internal encryption key.
Syntax
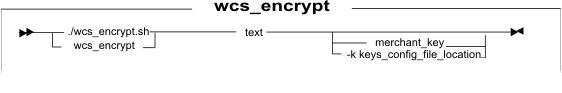
Parameter values
- text
- The character sequence to encrypt.


 Note: If
the value for the text parameter includes special characters, such
as '$', you must include the value within single quotation marks.
Note: If
the value for the text parameter includes special characters, such
as '$', you must include the value within single quotation marks. - merchant_key
- Optional: The value of the merchant key to encrypt the data. Specify this parameter if the merchant key is not retrieved from the Key Locator Framework.
- -k keys_config_file_location
- Optional: Retrieve the merchant key from the Key Locator Framework by using the specified key configuration file. Specify the absolute path of the file.
Example 1
Encrypt data when merchant key
is not retrieved from the Key Locator Framework: wcs_encrypt
abc 1234567890abcdef
Example 2
Encrypt data when merchant key
is retrieved from the Key Locator Framework: wcs_encrypt abc
-k C:\WebSphere\CommerceServer\instances\xml\CustomKeys.xml
Example 3
Encrypt data when the merchant key is not specified. In this case, an
internal encryption key is used, which is the same, regardless of the
version of WebSphere Commerce. For security
reasons, this key value is not shared. This usage is typically for
storing encrypted passwords in configuration files:
wcs_encrypt password


wcs_encrypt 'password'
The ASCII encrypted string should be stored in the configuration file.